Which type of password would be considered secure?
When creating an account on any website, you run into an inevitable dilemma: provide a weak but memorable password or a strong one that you will probably forget.
Table of Contents
Table of Contents
Following the guidelines and rules mentioned in this article will help you practice good password security. They have been successfully tried and tested by many internet users, and we strongly recommend you to follow them.
The anatomy of a good password
Here’s how to come up with a tough password that you won’t end up forgetting ten minutes later:
- Avoid short passwords. Create strong passwords that contain at least 10 characters. The more characters the password has, the longer it takes for a hacker to crack it.
- Make them complex. Password strength can be achieved by including upper and lower case letters, numbers and special characters. The more of them, the better. Learn more about password strength in our article on how to calculate password entropy.
- Use password managers. Long passwords are difficult to remember, especially when you have a different one for each website or service. You can use a powerful password manager like NordPass to help you organize your various login details.
- Create mnemonics. If tools for managing passwords are not your thing, create memorable phrases instead, making sure they relate to the website or service you’ll use them for. For instance, if you sign up for a VPN service to avoid the risk of cybercrime on public Wi-Fi networks, you could create a sentence like “I like to use NordVPN to protect my money” and use it as a mnemonic for the password “Il2uNV2pm$$$.” It includes all four types of characters, is complex, moderately long and easy to remember.
- Use passphrases (the Diceware method). Although using dictionary words is not advisable (see the tips for avoiding weak passwords below), creating a combination of 6-7 random words is a good method to protect your account. Randomness is the key, though. The human brain is extremely bad at stringing together truly random words, so the EFF website provides a list of numbered words. You roll a traditional game dice, and the numbers that come up choose the words for you. A combination like “right zebra fashion ultramarine football work” is extremely difficult to guess because of its length and randomness, but fairly easy to remember.
- Use a password generator. Try the NordPass random password generator to improve your password strength and create strong yet unique passwords. With this tool, you can create passwords ranging from 8 to 60 characters and use filters to add or avoid certain characters. Then, just copy your password straight to your NordPass password manager.
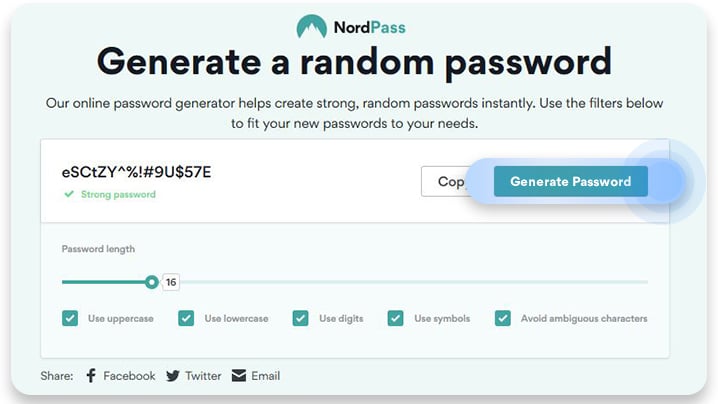
Simply following these tips would be a vast improvement and instantly increase your password strength. This is especially important for online banking and other financially sensitive websites.
Avoiding weak passwords
If you’ve ever asked yourself “how strong is my password”, we must emphasize that none of the following should ever be included in your passwords, even as one of the several components.
- The ‘name’ part of the username
- Names of friends, family members, pets, and especially your own name
- Personal information about your family members or yourself. That includes the general information that may be obtained very easily, such as phone number, birth date, street name, license plate number, house/apartment number, etc.
- A sequence of consecutive letters, numbers, or keyboard keys, such as “qwerty,” “12345,” “abcde,” etc.
- A dictionary word or a combination of words, such as “blackdog”
- Obvious substitutions, such as “blackd0g”
- Any of the mentioned above in reverse
- Blank password
PRO TIP: Make sure your password is at least eight characters long, if not longer. The security of a password really depends on its length. The longer the password is, the harder it is for a hacker’s software to guess.
Password common sense
Creating a strong password is crucial, but it’s only the initial step towards better security. The way you manage your passwords later on is even more important. Usually, people know the key rules, but somehow they tend to ignore them. Let this list be a friendly reminder that will help you keep your private information safe and secure.
- Create a unique password every time. When you change a password for any of your accounts, it should not be identical to any of the previous passwords. Oh, and don’t even think about setting the same password on different websites. While it is temping, try to resist and create unique passwords for each account.
- Change the passwords for all your existing accounts at least once every 6 months. Since passwords have a fixed length, a brute-force attack to crack a password will always be successful given enough processing power and time. Therefore, it is highly recommended to change passwords regularly. Schedule your calendar to remind you to change your passwords every 6 months.
- Do not share your password with anyone. That includes your family and friends. Also, never send an email with your password included in the text. Sometimes hackers send emails pretending to be a customer support agent and asking for your username and password. Legitimate organizations or websites never ask for your username and password via email.
- In case your password gets compromised, change it immediately. Even if you only suspect that someone might have stolen your password, change it right away. Every minute counts.
- Do not use the “Remember the password” browser option without setting a master password. If you do not set a master password in a browser, anyone using it will be able to see the stored password in plain text.
- Avoid typing your password on a device belonging to someone else. It is especially important for banking websites and business accounts. It is a common practice for hackers to log all keystrokes, which allows them to see everything you type, including your logins.
A strong password is just one part of your online defense. Secure yourself with NordVPN!